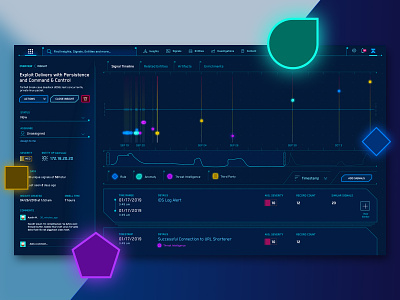
JASK's Sci-Fi Cyber Security Attack Timeline
This attack timeline aims to show security analysts the full story of a potential threat as it occurred over time where they can choose to investigate each signal at a time.
@Austin built this incredible brush so users could easily zoom in and out of time as they focus on particular events.
More by Harlan Elam View profile
Like